Technology
Nigeria’s Digital Quality of Life Index Declines to 100

Surfshark’s Digital Quality of Life Index (DQL) 2024 ranks Nigeria 100th in the world. The study indicates how well the country is performing in terms of overall digital well-being compared to other nations. Nigeria drops by twelve places from last year, which reflects a lack of commitment to developing the digital landscape and positioning the country as a leader in leveraging technological advancements to improve citizens’ quality of life.
“In an election year like 2024, where the digital realm shaped political discourse and societal values, prioritizing digital quality of life proved to be more important than ever. It helps to ensure informed citizens, protects democratic processes, and fosters innovation. Our annual project helps to better understand where each county stands in terms of digital divide, highlighting where a nation’s digital quality of life excels and where further focus is required,” says Tomas Stamulis, Chief Security Officer at Surfshark.
Out of the Index’s five pillars, Nigeria performed best in e-security, claiming 76th place, but faced challenges in e-infrastructure, ranking 108th. The nation ranks 94th in e-government, 103rd in internet quality, and 106th in internet affordability. In the overall Index, Nigeria lags behind South Africa (66th) and Kenya (89th). Collectively, African countries lag behind in their digital quality of life, Nigeria taking 14th place in the region.
Nigeria ranks lower in e-government than 77% of the countries analyzed, with 93 countries above.
E-government determines how advanced and digitized a country’s government services are. A well-developed e-government helps minimize bureaucracy, reduce corruption, and increase transparency within the public sector. This pillar also shows the level of Artificial Intelligence (AI) readiness a country demonstrates. Countries with the highest readiness to adopt AI technology are also ready to counter national cyberthreats. Nigeria ranks 94th in the world in e-government — six places lower than last year.
Nigeria is 76th in the world in e-security — three places lower than last year.
The e-security pillar measures how well a country is prepared to counter cybercrime and how advanced a country’s data protection laws are. In this pillar, Nigeria lags behind South Africa (75th) and Kenya (69th). Nigeria is unprepared to fight against cybercrime, the country has some data protection laws.
Nigeria’s internet quality is 25% lower than the global average.
- Nigeria’s fixed internet averages 39Mbps. To put that into perspective, the world’s fastest fixed internet — Singapore’s — is 347Mbps. Meanwhile, the slowest fixed internet in the world — Tunisia’s — is 14Mbps.
- Nigeria’s mobile internet averages 78Mbps. The fastest mobile internet — the UAE’s — is 430Mbps, while the world’s slowest mobile internet — Yemen’s — is 12Mbps.
Compared to South Africa, Nigeria’s mobile internet is 15% slower, while fixed broadband is 51% slower. Since last year, mobile internet speed in Nigeria has improved by 65%, while fixed broadband speed has grown by 55%.
The internet is unaffordable in Nigeria compared to other countries.
- Nigerians have to work 10 hours 43 minutes a month to afford fixed broadband internet. It is 46 times more than in Bulgaria, which has the world’s most affordable fixed internet (Bulgarians have to work 14 minutes a month to afford it).
- Nigerians have to work 2 hours 44 minutes 14 seconds a month to afford mobile internet. This is 18 times more than in Angola, which has the world’s most affordable mobile internet (Angolans have to work 9 minutes a month to afford it).
Nigeria is 108th in e-infrastructure.
Advanced e-infrastructure makes it easy for people to use the Internet for various daily activities, such as working, studying, shopping, etc. This pillar evaluates how high internet penetration is in a given country and its network readiness (readiness to take advantage of Information and Communication Technologies). Nigeria’s internet penetration is low (35% — 109th in the world), and the country ranks 102nd in network readiness.
On a global scale, investing in e-government and e-infrastructure improves digital well-being the most
Among the five pillars, e-government has the strongest correlation with the DQL index (0.92), followed by e-infrastructure (0.91).
Internet affordability shows the weakest correlation at 0.65.
METHODOLOGY
The DQL Index 2024 examines 121 nations based on five core pillars that consist of 14 indicators. The study is based on the United Nations’ open-source information, the World Bank, and other sources. Nigeria’s full profile in the 2024 Digital Quality of Life report and an interactive country comparison tool can be found here: https://surfshark.com/research/dql/country/NG.
Technology
Interswitch Advocates AI Adoption for Workforce Evolution

By Modupe Gbadeyanka
The Group Chief Human Resources Officer of Interswitch, Mr Franklin Ali, has called for the adoption of Artificial Intelligence (AI) to make work easier by boosting operational efficiency and driving economic growth.
Mr Ali, at the 2025 InnovateAI Conference Lagos held at the Landmark Centre, Lagos, submitted that, “The AI economy is a gateway to the knowledge economy, and it is imperative that we embrace this shift.”
“While AI adoption in leading economies like America and China remains below 50 per cent, these nations are at the forefront of AI advancements.
“To compete globally, Nigeria must prioritise reskilling and upskilling its workforce, fostering a mindset shift, and equipping professionals with core and enabling skills such as data literacy, JavaScript, and other technical competencies,” he further stated during a panel session titled AI and The Future of Work in Nigeria.
The Human Resources expert while emphasising the importance of targeted learning and problem-solving at the event themed Scaling AI Adoption in Nigeria: Catalysing Cross-Sectoral Innovation and Fostering Inclusive Growth, informed the participants that, “AI is not just a buzzword; it is a tool for solving real-world problems.”
“For instance, traffic congestion in Lagos is a challenge that can be addressed through AI-driven solutions.
“However, adept use of AI technology requires a deep understanding of core tech skills in areas like natural language processing, robotics, and machine learning.
“We must learn AI not for the sake of it but to solve specific problems that impact our society and economy,” he noted.
This year’s conference had Interswitch Group as a Platinum Sponsor for the second consecutive year, reinforcing its commitment to advancing AI-driven innovation across Africa.
By collaborating with key stakeholders and fostering industry-wide conversations, Interswitch aims to drive AI-powered innovation that will propel Nigeria’s digital economy forward.
As a pioneer in Africa’s fintech space, Interswitch remains dedicated to championing initiatives that harness technology’s transformative potential to unlock new opportunities, stimulate economic growth, and elevate user experiences.
Technology
YP4T Tasks Nigeria to Explore Opportunities in Digital Economy

By Aduragbemi Omiyale
The Nigerian government has been charged to quickly tap into the opportunities in the digital economy to help achieve the $1 trillion economy target of the administration of President Bola Tinubu.
This call was made by the Young Professionals for Tinubu (YP4T), which expressed delight over the willingness of the federal government to embrace artificial intelligence (AI).
The group warned that Nigeria must sustain these efforts to fully unlock the potential of AI-driven growth.
With a youth population expected to exceed 100 million by 2050, ensuring that young professionals have the skills, tools, and infrastructure to build AI-powered solutions is key to job creation and economic stability.
“As a network of young professionals actively engaged in shaping Nigeria’s future, we see these investments as fundamental to building a globally competitive workforce.
“This is not just about innovation; this is about securing economic opportunities for millions of young Nigerians. AI and digital transformation must be central to Nigeria’s long-term growth strategy, and every young Nigerian should be paying attention to these opportunities,” the Director of YP4T for West/South South, Mr Victor Benjamin, Stated.
“AI is no longer a theoretical concept—it is a defining force in global economies, and Nigeria is now actively securing its place in that future.
“For years, young Nigerians have sought opportunities in technology and digital innovation. What we are seeing now is a deliberate effort by the administration to turn that aspiration into reality through strategic policies, funding, and industry collaboration.
“This is a critical time for Nigerian professionals and businesses to position themselves in the AI-driven economy,” he added.
It has been projected that AI could add about $15 billion to the GDP of Nigeria if well-harnessed by the government through policies.
Recall that last week, Mr Tinubu held high-level discussions with the chief executive of Google, Mr Sundar Pichai, in France.
Talks also centred on the federal government 3 Million Technical Talent (3MTT) initiative, which has already begun producing a pipeline of AI-trained professionals, while the National AI Strategy Framework has laid the groundwork for AI integration across finance, agriculture, healthcare, and education.
Technology
Best Practices for Keeping Your CMS Updated and Secure
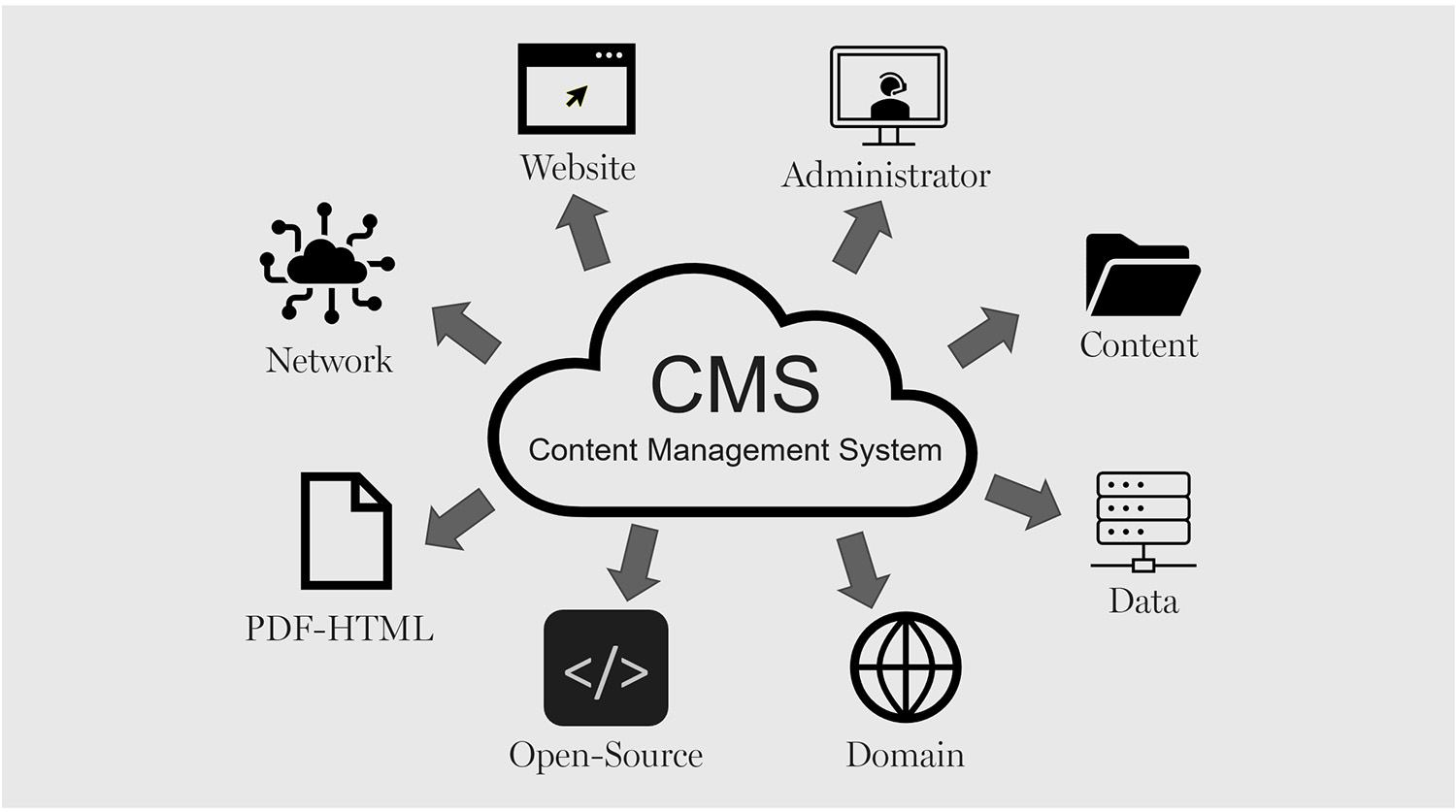
A Content Management System (CMS) drives many websites as it offers the best creation, maintenance, and deployment of digital content for an expanding enterprise. However, CMS can be an issue if not regularly updated or if security patches are bypassed. When hackers realize a CMS version is vulnerable, they attempt to breach it, gaining entry into a system to steal information or shut down a website.
A secure and reliable headless CMS requires constant updating, specific log-in and access, and continuous monitoring. Thus, a business that requires a secure CMS will ensure that client information is kept private, the experience is overall more seamless, and compliance is easier. This article outlines all the necessary updates and security patches to keep a secure and reliable CMS.
Regularly Updating CMS Core, Plugins, and Themes
One of the quickest ways to eliminate security vulnerabilities is by keeping the headless CMS core software and plugins/themes up to date. Developers are always updating for security vulnerabilities, enhancements of functionality, and added features. Failing to keep current opens a portal of exploitation for sites that developers have already fixed, making these sites low-hanging fruit for hackers. For example, if a retail business has a WordPress CMS for its website, and the WordPress CMS is outdated, it opens the site to being hacked.
There are WordPress fail issues that have not yet been addressed, which give hackers the chance to enter the system and add in malware. If a site has a lot of pending updates, many security vulnerabilities can be prevented. By checking often or setting up automatic updates, any business will have the most secure system possible. In addition, plugins or themes that are no longer supported by developers are ones to avoid as well. An unsupported plugin—with or without updates is a vulnerability, and it should be changed for something that gets consistent updates.
Strengthening Authentication and Access Control
A headless CMS such as the one that Storyblok provides usually has multiple users with different access levels. From administrators and editors to simple content creators, everyone can be a guest on the CMS. However, without access controls, a standard user can be granted administrative privileges either accidentally or on purpose and delete information or leave the CMS open for attack or intentional editing. Access control authorization relies on authentication. The ultimate protection for a CMS is multi-factor authentication. Multi-factor authentication reduces the likelihood of an account being compromised because it requires another form of validation aside from a username and password.
These can include one-time passwords or biometric fingerprints. Furthermore, implement super admin access to only what is necessary. If many team members need access to a project, role-based access (RBAC) gives everyone access only to what their job requires. The fewer the super admin accounts, the fewer the chances of insider threats and accidental security misconfiguration. Furthermore, the company should have password policies in place to require complicated passwords capitalization, numbers, special characters and employees should be educated on changing their passwords regularly. The chances of credential compromise are minimized with password managers.
Using Secure Hosting and Encrypted Connections
A headless CMS is only as good as its hosting. Should a company choose a reliable hosting service that includes security (firewalls, DDoS protection, malware scanning along with proper backup solutions), the company can maintain a secure level from the very beginning. On the other hand, unreliable hosts are vulnerable and subject to server-level attacks, which leave a site vulnerable to hacks and shutdowns. Another major component of security is a Secure Socket Layer (SSL) certificate, which protects all information sent from users to the site from prying third-party eyes.
With SSL encryption, this allows a company to avoid handing over to hackers any passwords, compromised personal information, or credit card numbers during those vulnerable transactions. Companies that deal with sensitive customer information needing additional security may opt for a managed hosting service with built-in, automated security management. Managed hosting services are more likely to secure vulnerabilities, watch for nefarious activity, and perform security hardening so these companies don’t have to delegate duty.
Conducting Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability scans uncover vulnerabilities in a headless CMS before a hacker gets the chance to exploit them. Security audits ensure correct user permissions, potential database corruption, and server configurations so that no unintended levels of access exist. For example, a content-managed eCommerce site should assess how often rogue administrators can access the CMS via security audits to avoid malicious penetration that could lead to poor choices. Thus, a content-managed eCommerce site wants to ensure that accidental charge transactions do not happen on the checkout function, so a vulnerability scan is regularly required.
Security plugins within the headless CMS and external vulnerability scanning websites provide assessments of malware injections, brute force login attempts, and unnecessary file permissions. Furthermore, simply keeping an eye on the CMS logs to check for oddities, surprising login attempts, changes in core files, individuals visiting the admin panel when they should not be granted visibility would keep a company apprised of its security. An apprised awareness of security would avoid a lot of exploits from escalating into a massive cybersecurity event.
Implementing a Reliable Backup Strategy
Fail-safe backup solution. Even with the most secure CMS, there’s always a chance that a hack or malfunctioning headless CMS occurs or even a wipe happens accidentally. A backup solution that is fail-safe ensures that no matter what type of catastrophic security issue occurs on the site, it can be restored with ease and no major downtime. Backup should be automatic and regular, off-site or an encrypted cloud solution. This ensures that even if the primary server is hacked, nothing is lost. A backup solution should encompass full database, full file, and full configuration backups for the CMS to guarantee that everything is restorable when needed.
For example, a headless CMS-centric, news-driven site and a digital asset manager are hacked and all posts are erased. They’ll be restored in a flash unless the backup from last night is still there. These types of restorations need to be regularly tested to confirm they are there and up to date.
Securing API Integrations and Third-Party Extensions
Many CMS have third-party applications, payment processors, and other services via API integrations for extended functionality. However, these integrations are potential weaknesses that hackers can infiltrate without proper security protocols. All API integrations should require secure authentication encrypted API keys and OAuth tokens and unauthenticated services should never have unrestricted access to sensitive data. Furthermore, only externally developed plug-ins and extensions should be used and those created by trusted developers and extensively vetted; antiquated, unpoliced third-party applications can open disastrous loopholes.
Of course, being a financial center, a headless CMS for investment and sourcing and getting reputable user information should have all third-party APIs and financial integrations assessed for security compliance to prevent data leaks or accidental purchases. By assessing and strengthening these external integrations, companies reduce the risk that additional vulnerabilities will penetrate the CMS ecosystem from the outside.
Monitoring and Responding to Cyber Threats
Yet regardless of how bulletproof a site may be, the ideal method of learning about and addressing cybersecurity weaknesses will always be preemptive and responsive awareness. Thus, companies need to adopt further real-time security monitoring to be notified of nefarious actions, unauthorized logins, and breaches. For example, a retail website’s enterprise content management system should include intrusion detection systems (IDS) and web application firewalls (WAF) to prevent accidental access from those who don’t belong or to prevent interactions with bots.
In addition, a cyber incident response plan ensures that there are trained protocols for rapid response if a breach were to happen. For instance, an incident response plan dictates that one must quarantine affected machines, roll back to backups, notify stakeholders, and determine how to prevent this from happening again. This level of understanding empowers organizations to be ahead of the game and mitigate as much destruction to their content management systems that cyber intrusions would create.
Conclusion
A maintained, safe CMS is not static. There are security updates, there is testing and debugging, and vulnerabilities are always there. Thus, for these enterprises that fail to secure their CMS systems, the chance for attacks is great resulting in breaches and costly downtime, which creates not only chaos in brand identity but in the company’s balance sheet. These measures minimize exposure and build a resilient, secure environment when organizations change default CMS files, update passwords, enhance server security, and engage in security audits.
Secure API integrations, knowledge of cybersecurity developments, and the ability to restore backups reliably, create a CMS more resistant to ever-increasing threats. A secure Content Management System essentially protects vital proprietary and customer data and keeps sites up and running with appropriate user confidence. Firms with a comprehensive Content Management System security strategy render their businesses transferable to the digital arena with more growth potential and less concern for cyber attacks.
-

 Feature/OPED5 years ago
Feature/OPED5 years agoDavos was Different this year
-
Travel/Tourism9 years ago
Lagos Seals Western Lodge Hotel In Ikorodu
-

 Showbiz2 years ago
Showbiz2 years agoEstranged Lover Releases Videos of Empress Njamah Bathing
-

 Banking7 years ago
Banking7 years agoSort Codes of GTBank Branches in Nigeria
-

 Economy2 years ago
Economy2 years agoSubsidy Removal: CNG at N130 Per Litre Cheaper Than Petrol—IPMAN
-

 Banking2 years ago
Banking2 years agoFirst Bank Announces Planned Downtime
-

 Sports2 years ago
Sports2 years agoHighest Paid Nigerian Footballer – How Much Do Nigerian Footballers Earn
-

 Technology4 years ago
Technology4 years agoHow To Link Your MTN, Airtel, Glo, 9mobile Lines to NIN